Meltdown cpu hardware vulnerability bug isometric composition with computer system board and malicious software symbol vector illustration Stock Vector Image & Art - Alamy

A standard IoT model with hardware vulnerabilities. This paper focuses... | Download Scientific Diagram
Researchers discover a new hardware vulnerability in the Apple M1 chip | MIT News | Massachusetts Institute of Technology
Hardware Vulnerability Icon in Flat Style on Transparent Background Stock Vector - Illustration of hack, microprocessor: 130891355






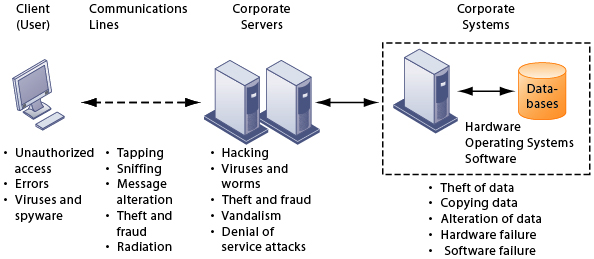


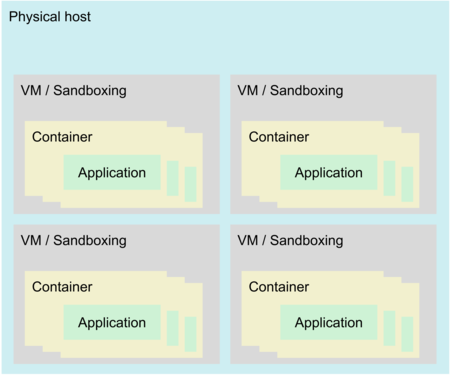



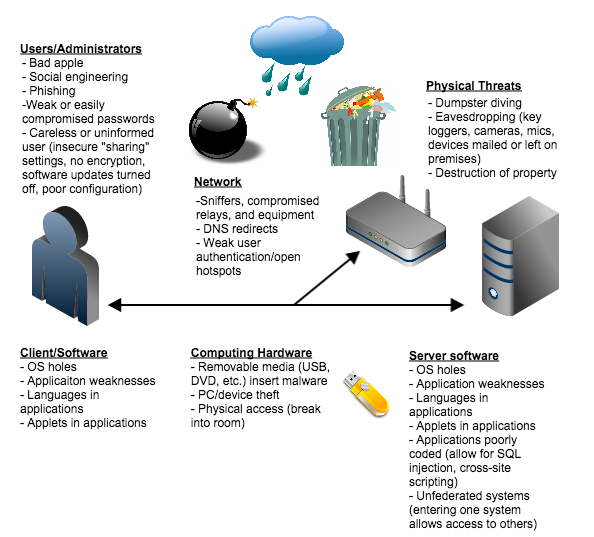
![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/5-Figure3-1.png)