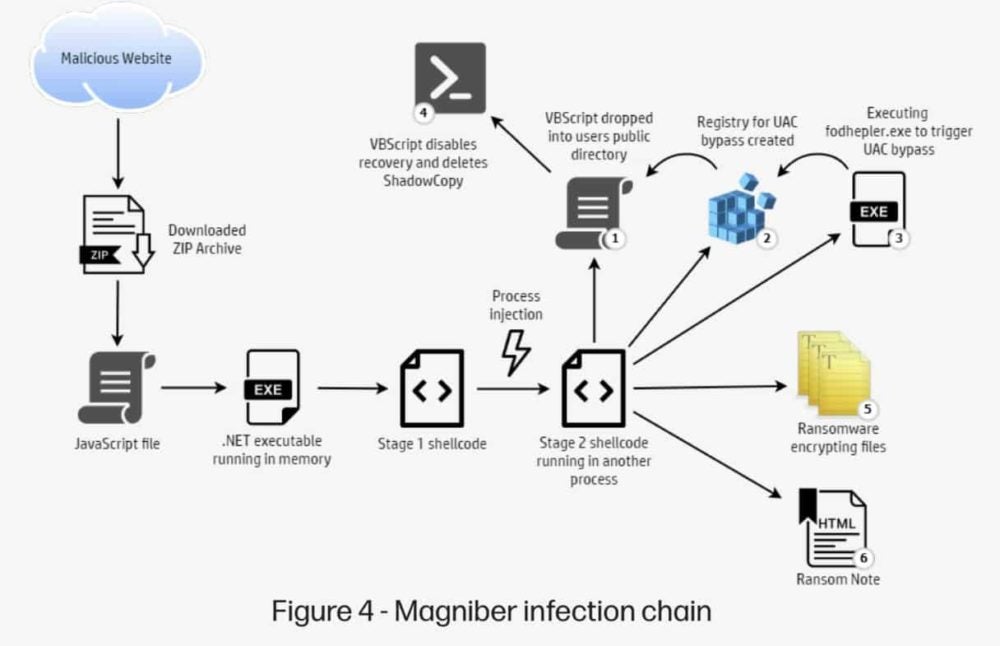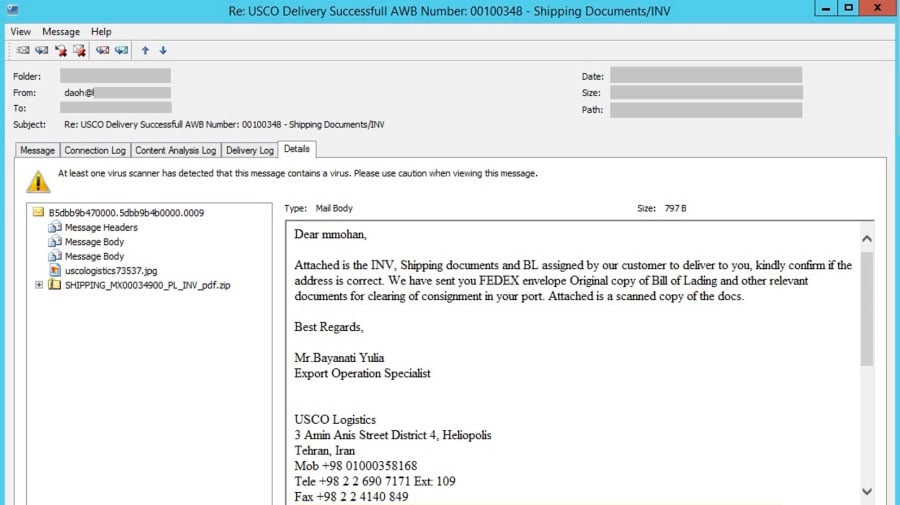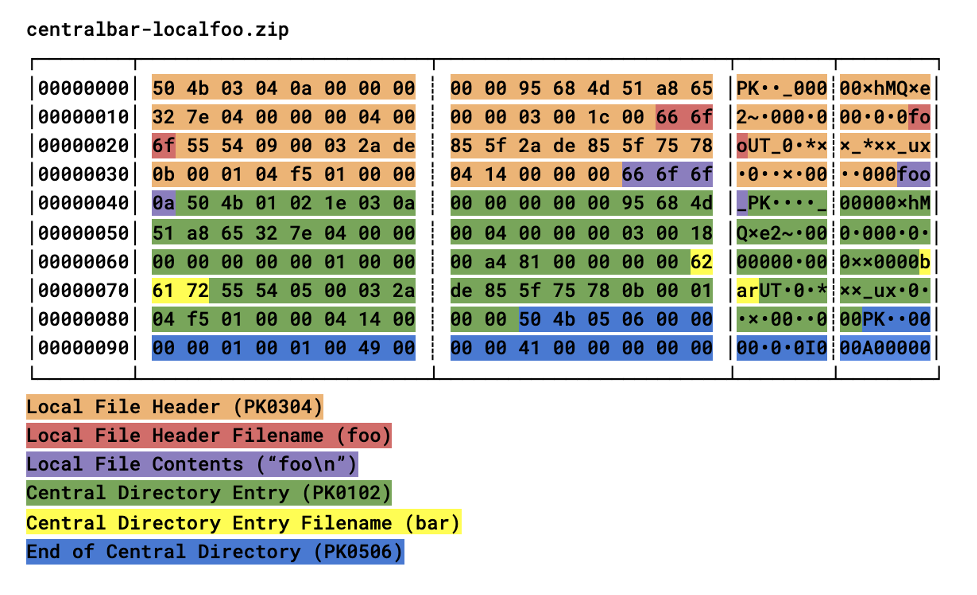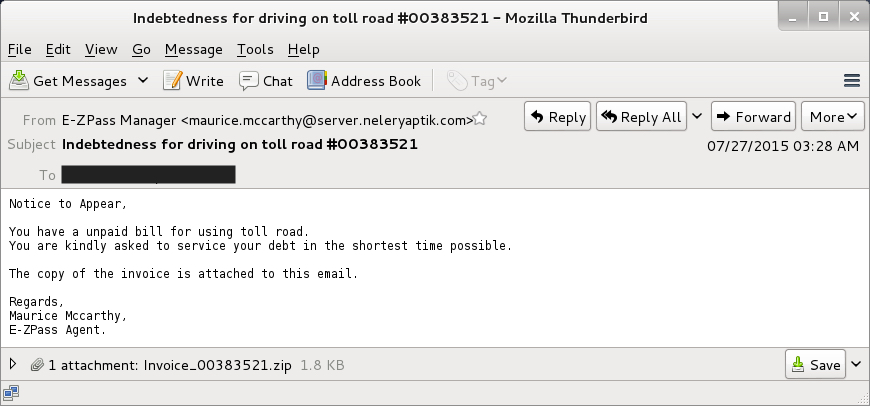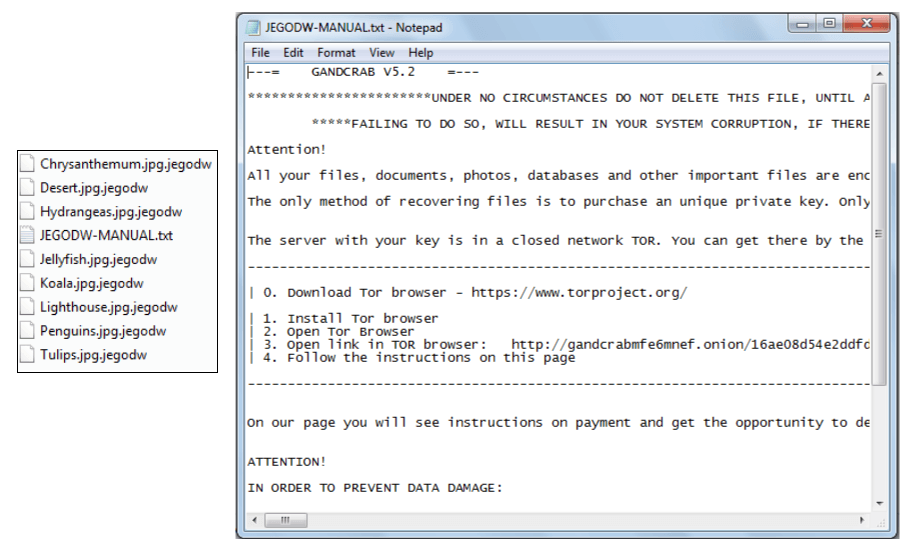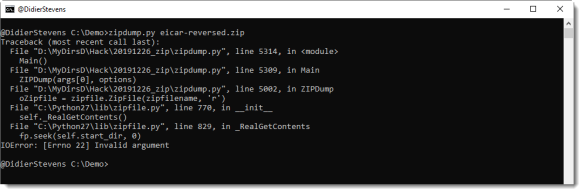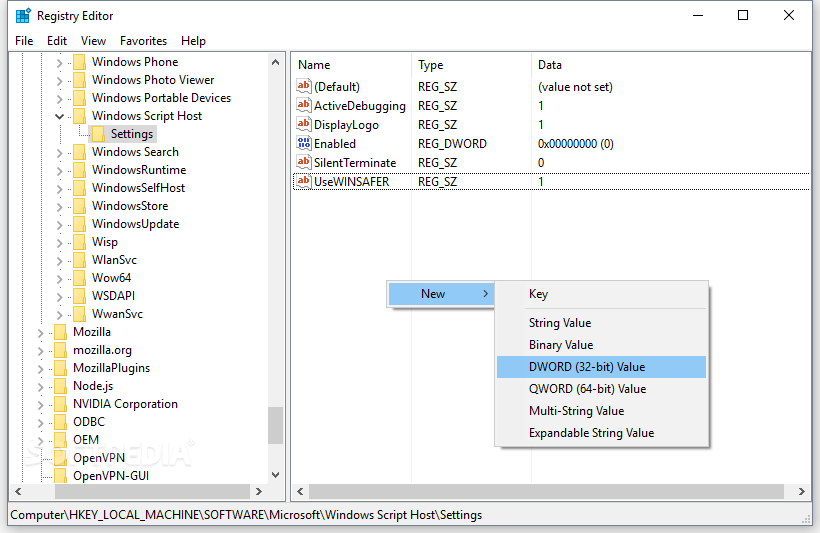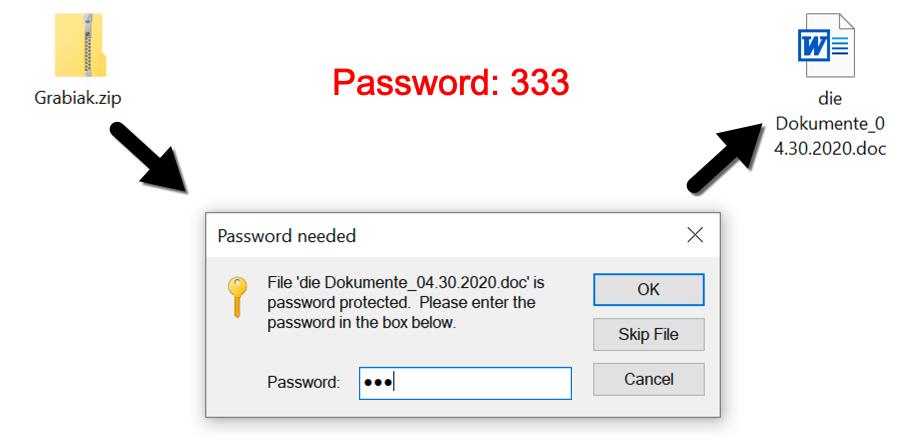
Malware-Traffic-Analysis.net - 2020-04-30 - Password-protected zip files from German malspam push Dridex

HTML smuggling surges: Highly evasive loader technique increasingly used in banking malware, targeted attacks | Microsoft Security Blog
TIL that there is a malicious zip file on the internet that is only 42 kilobytes when compressed, but 4.5 petabytes when unzipped (that's 4500 terabytes or 4,500,000 gigabytes!) : r/todayilearned

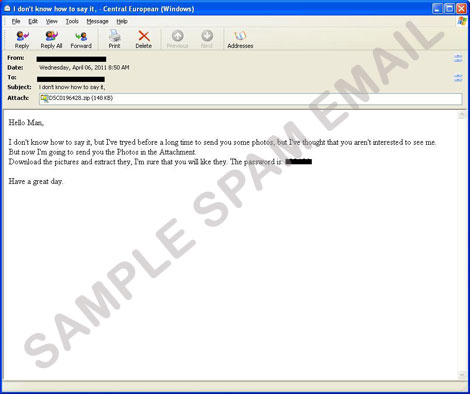
Hoax-Slayer on Twitter: "Watch for emails claiming that an account has expired. The emails have an attached zip file and contain a supposed password for access. Opening the file can lead to