![Hardware Vulnerabilities and Their Effects on CE Devices: Design for Security Against Trojans [Hardware Matters] | Semantic Scholar Hardware Vulnerabilities and Their Effects on CE Devices: Design for Security Against Trojans [Hardware Matters] | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d3581b246920cfa5aacce09f0f344eeb68d157a8/3-Figure3-1.png)
Hardware Vulnerabilities and Their Effects on CE Devices: Design for Security Against Trojans [Hardware Matters] | Semantic Scholar

Hardware Vulnerabilities: How You Can Do Everything Right And Still Be Compromised | by Rohan Kulkarni | PALOIT | Medium
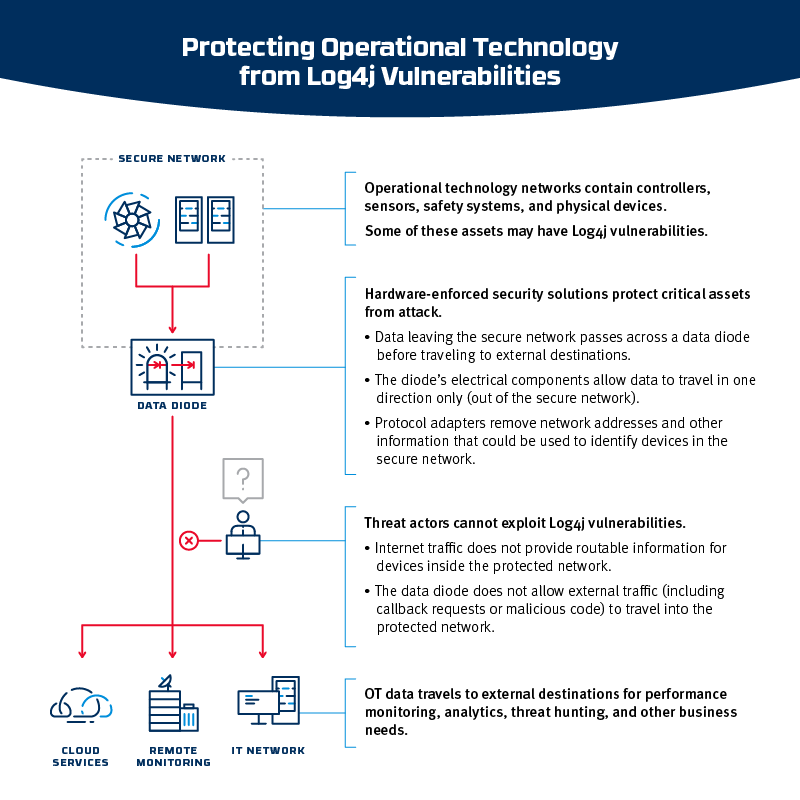
Defending Against the Unknown: Hardware-Enforced Security and Zero-Day Vulnerabilities | Owl Cyber Defense
Researchers discover a new hardware vulnerability in the Apple M1 chip | MIT News | Massachusetts Institute of Technology