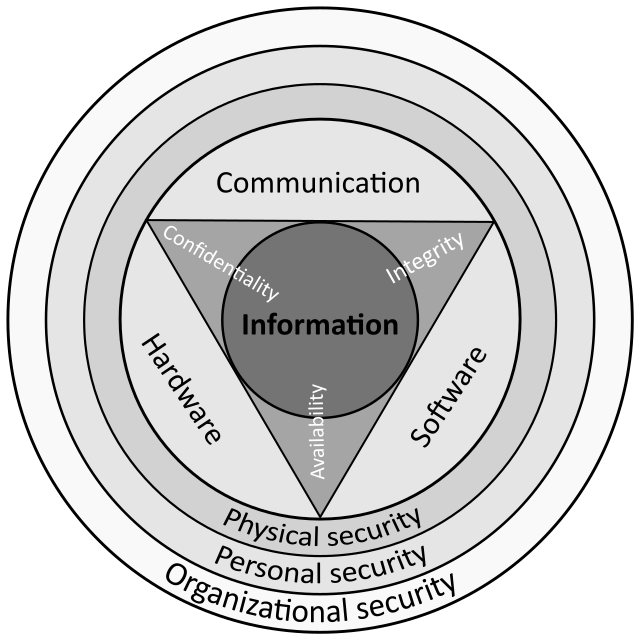
Hardware Vulnerabilities: How You Can Do Everything Right And Still Be Compromised | by Rohan Kulkarni | PALOIT | Medium

Sensors | Free Full-Text | A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
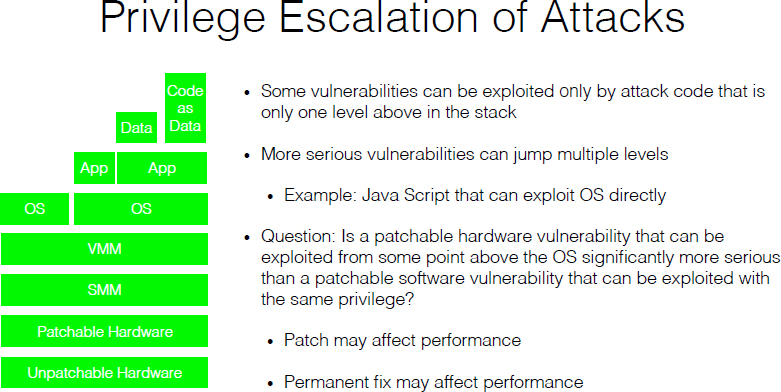
2 Hardware and Software Engineering Assumptions at Risk | Beyond Spectre: Confronting New Technical and Policy Challenges: Proceedings of a Workshop |The National Academies Press

As firmware-level threats continue to gain popularity in the wild, security teams need to understand how these threats work and the real-world risks they pose to an organization's security. Updated for 2021,